We describe in 5 steps how to protect your business against DDoS attacks of any size.
How to prevent and mititgate DDoS part 1?
We all heard about DDoS and we all fear them. We all hope to never be a victim of hackers or be ask for a ransom in exchange to not be DDoS. The day it’s happening to you, you realize it’s too late. You call your ISP and they tell you it will costs 3000$[…]
How to install a software without spyware?
There was a time when installing software was just a matter of clicking next a couple of times and then finish. The most difficult part was to accept the license agreement because we couldn’t click next until we accept it. We could install as many software as we want without worrying on spywares and malwares.[…]


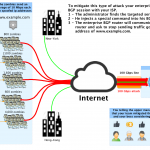 How to Protect Successfully your network against DDoS attacks: 5 steps
How to Protect Successfully your network against DDoS attacks: 5 steps